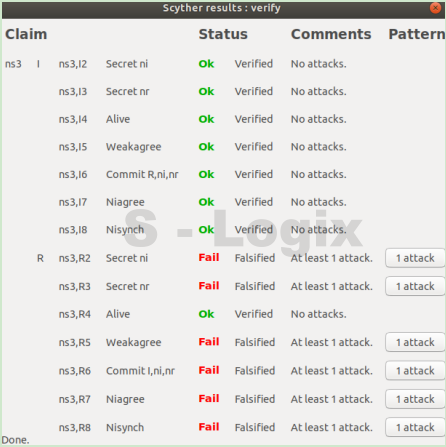
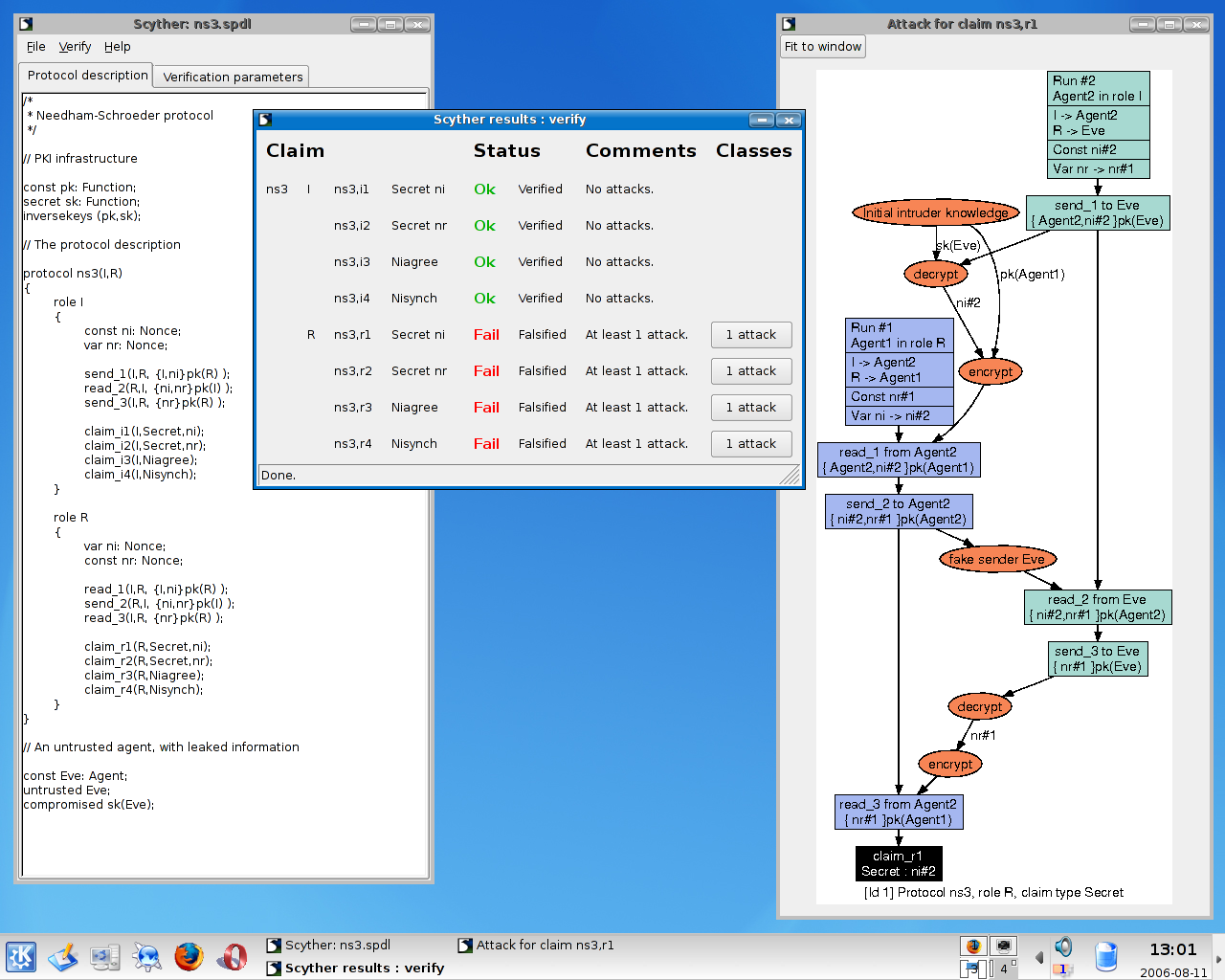
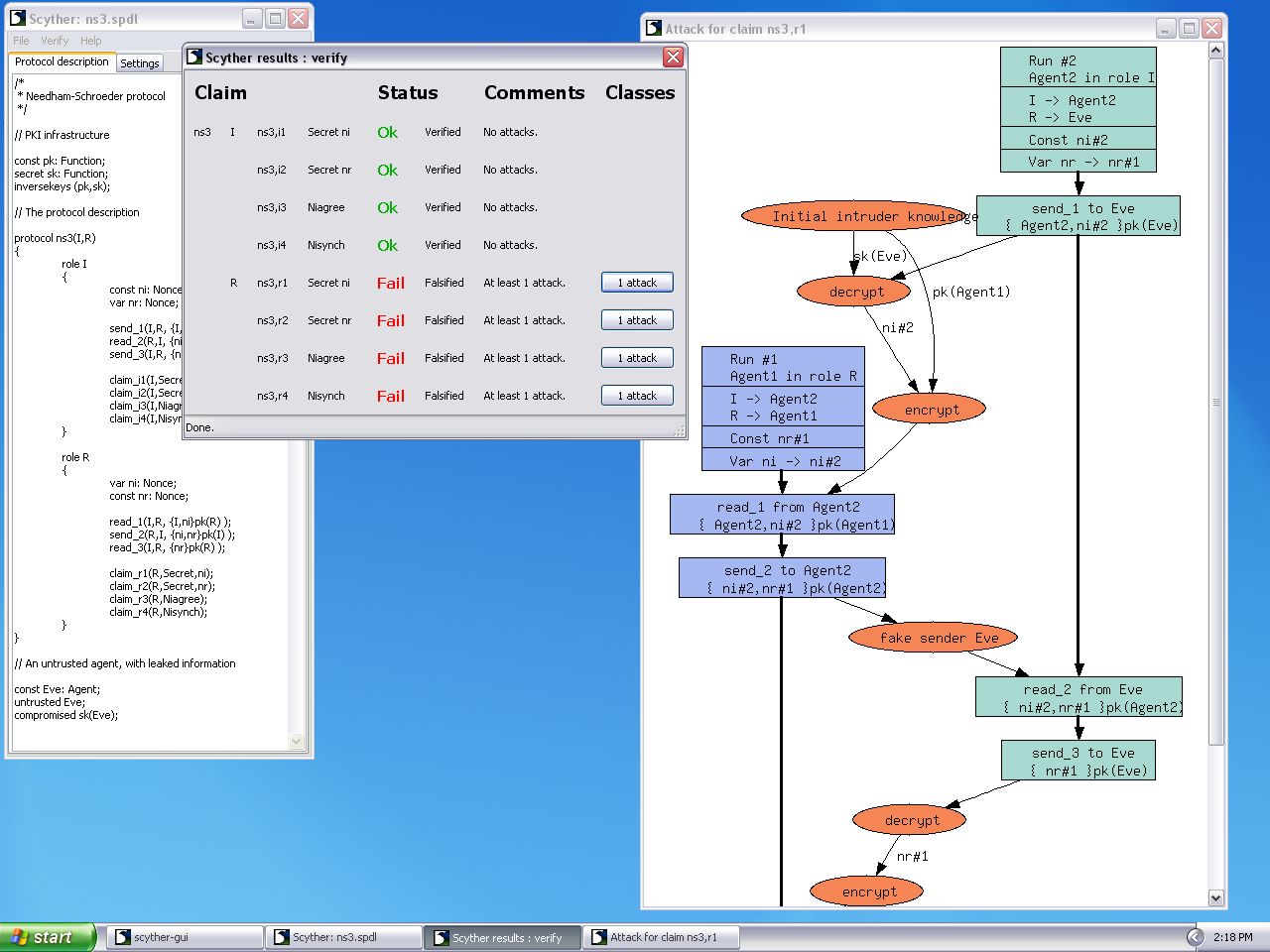
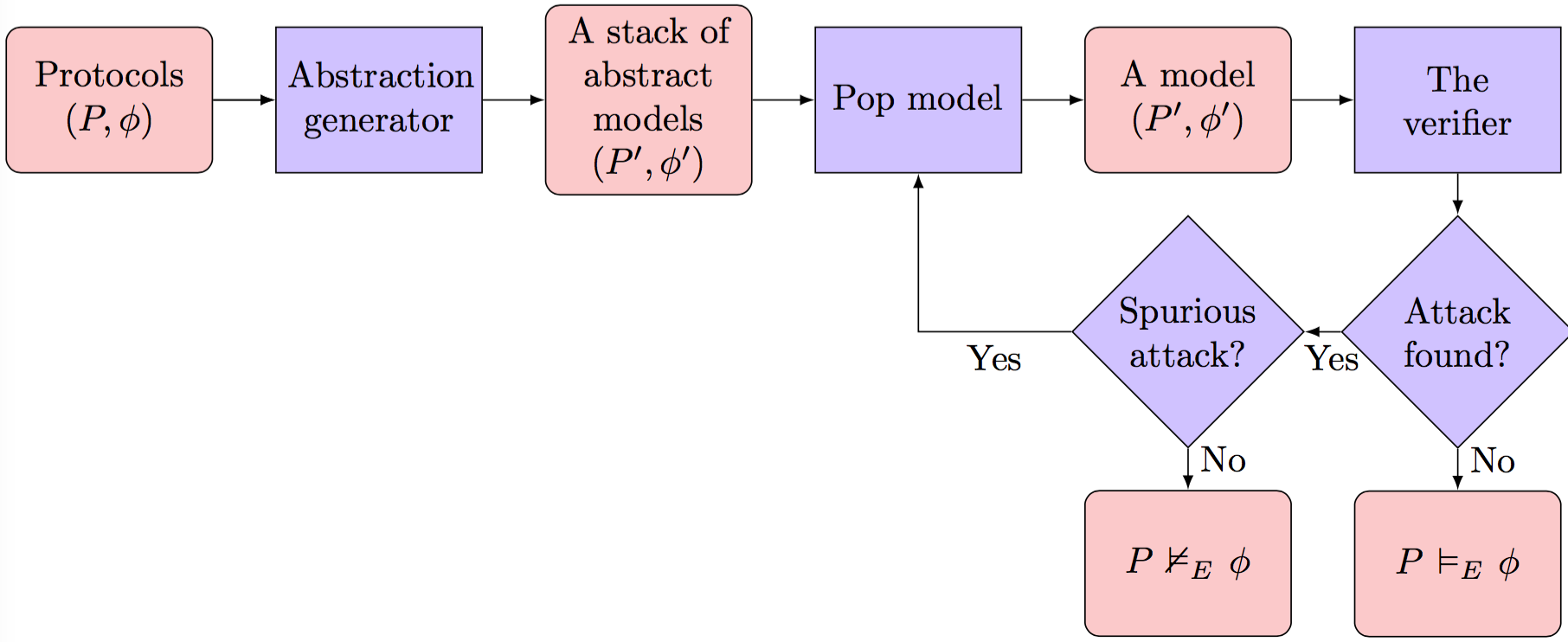
Simulation results of the Scyther tool. Figure includes two pictures.... | Download Scientific Diagram
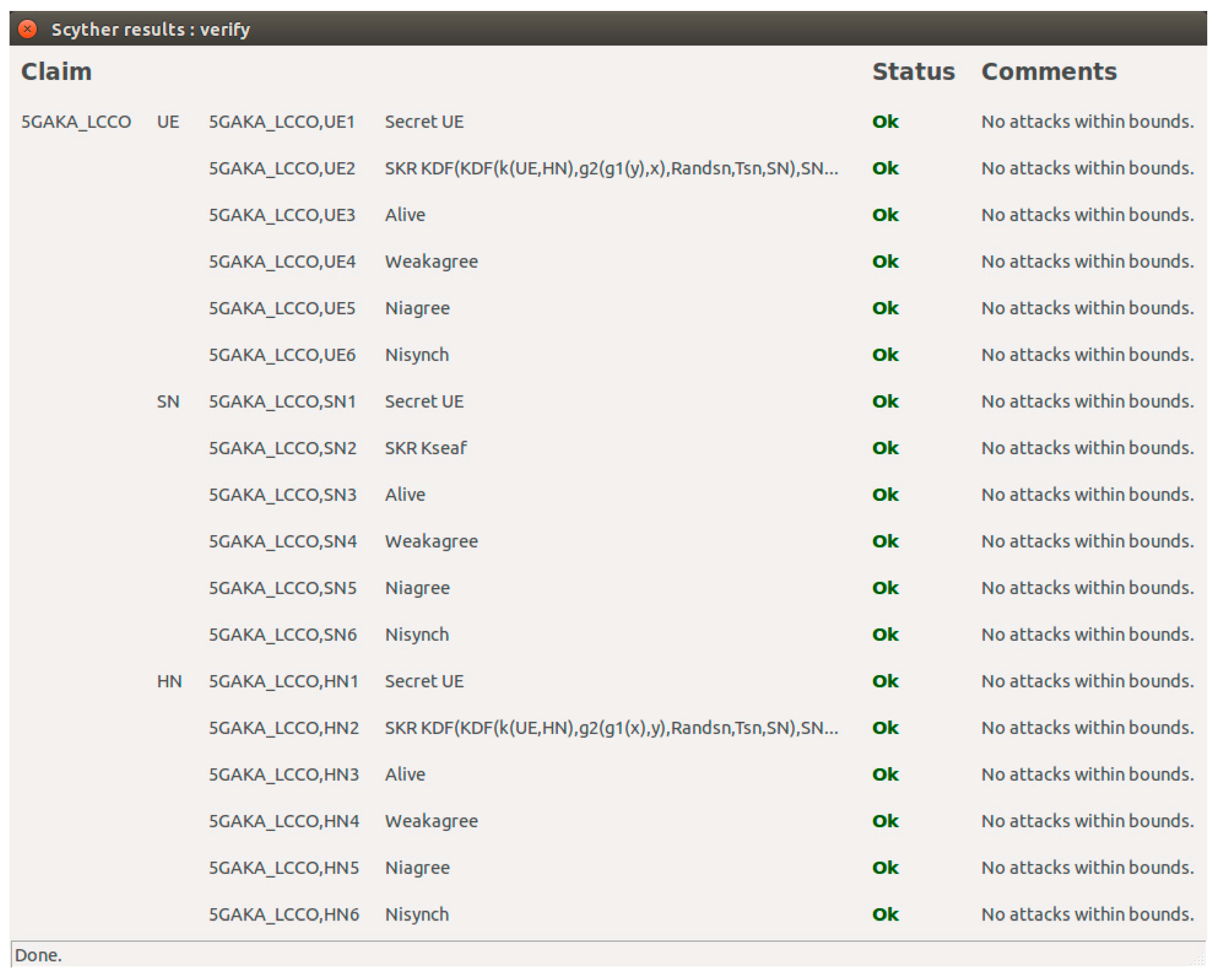
Information | Free Full-Text | 5GAKA-LCCO: A Secure 5G Authentication and Key Agreement Protocol with Less Communication and Computation Overhead
A Strong Mutual Authentication Protocol for Securing Wearable Smart Textile Applications. - Document - Gale Academic OneFile

An efficient authentication and key agreement protocol for IoT-enabled devices in distributed cloud computing architecture | EURASIP Journal on Wireless Communications and Networking | Full Text

A privacy-preserving handover authentication protocol for a group of MTC devices in 5G networks - ScienceDirect